July 17, 2011
In corporate environment more and more knowledge workers are using Smart Phones & Tablets. Virtualised working environment is developing. Geographically dispersed professionals are working through collaboration tools. Technologies such as Video conferencing, IP Telephony, Portal, Virtual Client, and Cloud etc.. Smart Phones & Tablets are catering the requirement to work remotely and virtually.

Smart Phones & Tablets to Work
Last week I read the Toastmaster Magazine June 2011 edition. Article “Presentations TO GO!” Written by Dave Zielinski describing about couple of tools which useful for presentations and toastmaster speeches. That is the thread I’m presenting here.
Applications which are supports smart phones & tablets. Those applications are very useful to work from smart phones & tablets. I’m listing those applications below.
- Keynote Presentation Design Software
- Documents to Go
- ThinkFree Mobile
- Prompster
- ProPrompter
- SpeechPrompter
- Dragon Dictation


25.271139
55.307485
Posted in CLOUD, Communication, Management, MOBILE, Network, Technical, Virtualization, VPN |
Leave a Comment »
July 10, 2011
There are so many hacks happened in recent days. That to major corporate organisations key databases. During the IDC security road show, Dubai (21-06-2011) one of the presenters was showing a slide with some corporate logo, captioned as it’s not our customer list. It’s giving high alert to business and professionals. How to protect the critical information? Is there any one product to buy and keep as security? Lot of questions and fears! Where to protect, what to protect and how to protect. To whom we can trust, to whom we cannot. Security road show I saw another interesting caption don’t trust anyone. To build up a security systems, the primary factor is awareness. What is our critical information’s, who all have access now, how they access, where it’s kept, how it’s kept, etc. Once we have the awareness, start putting technology to protect each of the segments. Keep a proper discipline. It has to be reviewed frequently and improved.

Key to Security


25.271139
55.307485
Posted in Backup & Restore, CLOUD, Communication, Data Center, Management, MOBILE, Network, Security, Technical, Virus |
Leave a Comment »
June 22, 2011
Google Cloud Connect for Microsoft Office is one of the collaboration services from Google. It’s really picking up market. It allows two or more people work together on the same file at the same time in Microsoft Office 2003, 2007 or 2010 on Windows PCs. For example, you can edit a Word document’s table of contents from one office while co-workers adjust formatting and make revisions from another office. Instead of bombarding each other with attachments and hassling to reconcile people’s edits, your whole team can focus on productive work together.

Google Cloud Connect for Microsoft Office
- Simultaneous editing for Word, PowerPoint and Excel files, no document or paragraph locking
- Google Docs sharing URLs for each Microsoft Office file
- Revision history for Microsoft Office files, stored in Google Docs
- Offline editing with smart synchronization of offline changes
- No Microsoft Office upgrade or SharePoint® deployment required

25.271139
55.307485
Posted in CLOUD, Communication, Management, MOBILE, Virtualization |
Leave a Comment »
March 10, 2011
I had a chance to attend the conference (09-03-2011). It was rich contented and lot of thought process in different angles. Its benefits, commercials, challenges, security, legal and future. One thing sure the drive is towards cloud, it’s private, public and hybrid. Cloud computing is there the time internet started or the mainframe started. Now the service delivery models changed. Tomorrow this service can call it as different name with some added value or modifications. Discussion of PaaS, IaaS, SaaS was fruitful and given thought of the service model. Cloud model has CAPX and OPX benefits. But it’s depends the maturity of the organization or how the approach is. Couple of challenges related to this region discussed about the connectivity, legal aspects and security. More and more players coming this market with different service design. The concept still to go for more maturity and definitions. Virtualisation, consolidation, thin clients are the couple of components making this journey. Anywhere any time access. Optimization and de-duplication also part in it.

Cloud Computing World Forum Middle East and Africa in Dubai
25.271139
55.307485
Posted in Communication, Data Center, Management, Network, Security, Technical, Virtualization |
Leave a Comment »
March 3, 2011
Users have been exposed to the risks of sending data over the Internet while at the same time having the expectation that telephone conversations are strictly confidential. Security issues in the data and voice networks are in fact very similar, but completely separate in the minds of most users. Major security concerns of VOIP networks.
• Phreaking
Phreaking is a slang term coined to describe the activity of a subculture of people who study, experiment with, or explore telecommunication systems. This is sometimes called the H/P culture (with H standing for hacking and P standing for phreaking). Through this making calls through another user network, putting cost to that person.
• Eavesdropping
Eavesdropping is how most hackers steal credentials and get important information like business data. Through eavesdropping, a third party can obtain names, password and phone numbers, allowing them to gain control over voicemail, calling plan, call forwarding and billing information.
• Vishing
Vishing is a party calling you faking a trustworthy organization (e.g. your bank) and requesting confidential and often critical information.
• DoS (Denial of Service)
DoS attacks can be carried out by flooding a target with unnecessary SIP call-signaling messages, thereby degrading the service.
• SPIT (Spamming over Internet Telephony)
SPIT attacks consist of sending a voicemail to a person, masquerading it with information from a party trustworthy to the receiver, like a bank or online paying service, making him think he is safe.
• Man-in-the-middle attacks
VoIP is particularly vulnerable to man-in-the-middle attacks, in which the attacker intercepts call-signaling SIP message traffic and masquerades as the calling party to the called party, or vice versa. Once the attacker has gained this position, he can hijack calls via a redirection server.
25.271139
55.307485
Posted in Backup & Restore, Communication, Network, Security, Technical |
Leave a Comment »
January 10, 2011
Technology and concept is changing day by day. New strategy and solutions. Interaction and integration is vital everywhere. To thrive in today’s economy, you have to collaborate with colleagues, partners, and customers around the globe at a moment’s notice. At the same time, you want to conduct your business in a way that enhances the quality of your relationships. Here are numerous applications for telepresence, ranging from corporate conferencing to remote surgery. It is actively used for both of these things, and can also be seen in the education field, using telepresence to connect educators, students, and professionals across varying distances. Some companies also use telepresence in dangerous spaces, such as under the sea or deep within the Earth, to allow employees to visit the site without putting themselves at risk. As the technology is refined, developers claim, people could use telepresence to visit archaeological sites without damaging them, or to take trips to distant regions.
Read More:-
1. Cisco Telepresence
2. Polycom Telepresence
3. Telepresence World
25.271139
55.307485
Posted in Communication, Management, Network, Technical, Virtualization |
Leave a Comment »
August 17, 2009
Microsoft Office Communicator is a unified communications application that helps end users be more productive by enabling them to communicate and collaborate easily with others in different locations or time zones using a range of different communication options, including instant messaging (IM), voice, desktop sharing and video. Integration with programs across the Microsoft Office system — including Word, Excel, PowerPoint, OneNote, Groove, and SharePoint — gives end users many different ways to communicate directly from the context of their task.
- Simplify communications with immediate presence awareness.
- Let others know the best way to contact you.
- Manage your contacts more easily.
- Choose the communication method that meets your needs.
- Access powerful phone features through your PC.
- Work faster with intuitive device integration and support.
- Quickly communicate from Microsoft Office applications.
- Take advantage of familiar tools to improve productivity
- Keep a conversation history.
- Connect and communicate from the location of your choice
- Convenient access through multiple devices

Posted in Communication, Technical |
Leave a Comment »
August 5, 2009
DMVPN is a simple, secure, low cost, scalable VPN-Tunnel. DMVPN supports distributed applications including: data, voice, and video, with QoS. All of this can be done in a secure IPSec VPN tunnel over an Internet connection. The only change is the IP address of the GRE Tunnel. The spoke uses dynamic discovery of IPSec tunnel end-points, (other spokes). No IPSec static configuration for each spoke.
Because DMVPN supports multipoint GRE tunneling you can run VoIP, Video, and Multicast services across your secure DMVPN link. Hub-and-Spoke, (H&S) and Spoke-to-Spoke, (S2S). With H&S the design.
It’s a cost effective and secure communication for branch offices.
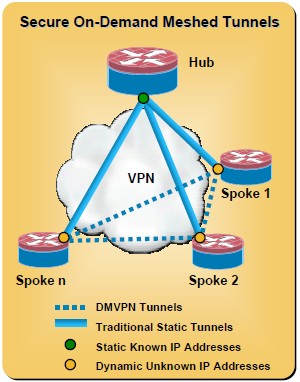
DMVPN Overview
Posted in Communication, Network, Technical, VPN |
2 Comments »
July 29, 2009
Unified communication is an industry term used to describe all forms of call and multimedia/cross-media message-management functions controlled by an individual user for both business and social purposes. This includes any enterprise informational or transactional application process that emulates a human user and uses a single, content-independent personal messaging channel for contact access.
The essence of communication is breaking down barriers. In its simplest form, the telephone breaks distance and time barriers so that people can communicate in real time or near real time when they are not together. There are now many other barriers to be overcome. People can use many different devices to communicate (wireless phones, personal digital assistants, personal computers, thin clients, etc.), and there are now new forms of communication as well, such as instant messaging. The goal of unified communications involves breaking down these barriers so that people using different modes of communication, different media, and different devices can still communicate to anyone, anywhere, at any time.
Unified communication (UC) encompasses several communication systems or models including unified messaging, collaboration, and interaction systems; real-time and near real-time communications; and transactional applications.
- Unified messaging focuses on allowing users to access voice, e-mail, fax and other mixed media from a single mailbox independent of the access device.
- Multimedia services include messages of mixed media types such as video, sound clips, and pictures, and include communication via short message services.
- Collaboration and interaction systems focus on applications such as calendaring, scheduling, workflow, integrated voice response, and other enterprise applications that help individuals and workgroups communicate efficiently.
- Real-time and near real-time communications systems focus on fundamental communication between individuals using applications or systems such as conferencing, instant messaging, traditional and next-generation private branch exchanges.
- Transactional and informational systems focus on providing access to m-commerce, e-commerce, voice Web-browsing, weather, stock-information, and other enterprise applications.
Cisco Unified Communications
Posted in Communication, Technical |
Leave a Comment »
July 2, 2009
Recession gave me to start thinking about cost effective communication solution. In corporate and SMB environment communication cost is one of the major portion of operational cost. Communication can’t be avoided, so how we can reduce with using other effective solutions. Consider the legal aspects, cost of infrastructure, management, maintenance, expertise requirement.
In a run through the present office scenario, we have lot of single man office or mobile office. That too spread across. All the users required to access different services. Some of them are in house hosted or some of them are from internet. Companies are integrated the work flow through the devices. Here users are using different gadgets, laptop, soft phone, note book, Black Berry, I Phone, etc.
All the areas communication cost is an integral one. The ways of cost involved is different ways. Internet charges, telephone charges, leased line cost, ADSL cost, LAN phone cost, mobile phone cost.
Couple of Solution:-
- Office Communicator
- Open Source SIP based Unified Communication
- VPN over ADSL to ADSL
- BlackBerry
These are just high level of technologies, work each solutions depends on the size of organization, requirement, infrastructure availability, skill set. A detailed exercise required. Out of the box, the solutions give you a major reduction in communication cost.
Posted in Communication, Network, Technical |
Leave a Comment »

 Follow Me
Follow Me LinkedIn
LinkedIn Facebook
Facebook













